In the online world, protecting one’s account credentials is the top priority right now. Using a username and a random, secure password is a good place to start, albeit it is not a complete security measure either. Two-factor authentication has been the norm for quite some time now, although some companies are raising the bar. Three-step authentication provides even more security, but some people might see it as a cumbersome security measure as well.
Do We Need Three-Step Authentication?
That seems to be the biggest question right now. A lot of consumers – and some enterprises – still rely on using just a username and password for authentication purposes. Despite a growing number of data breaches affecting this authentication combination, it appears there is little interest in increasing overall security. It has become significantly easier to protect our online credentials, though.
Two-factor authentication has become the norm in the online world for quite some time now. Desktop users often authenticate through a 2FA client, which comes in the form of a code sent via email or SMS. Other solutions, such as Google Authenticator and Yubikey, have also gained widespread adoption. For all of these additional security measures can be used free of charge, there is no reason not to enable two-factor authentication whenever and wherever possible.
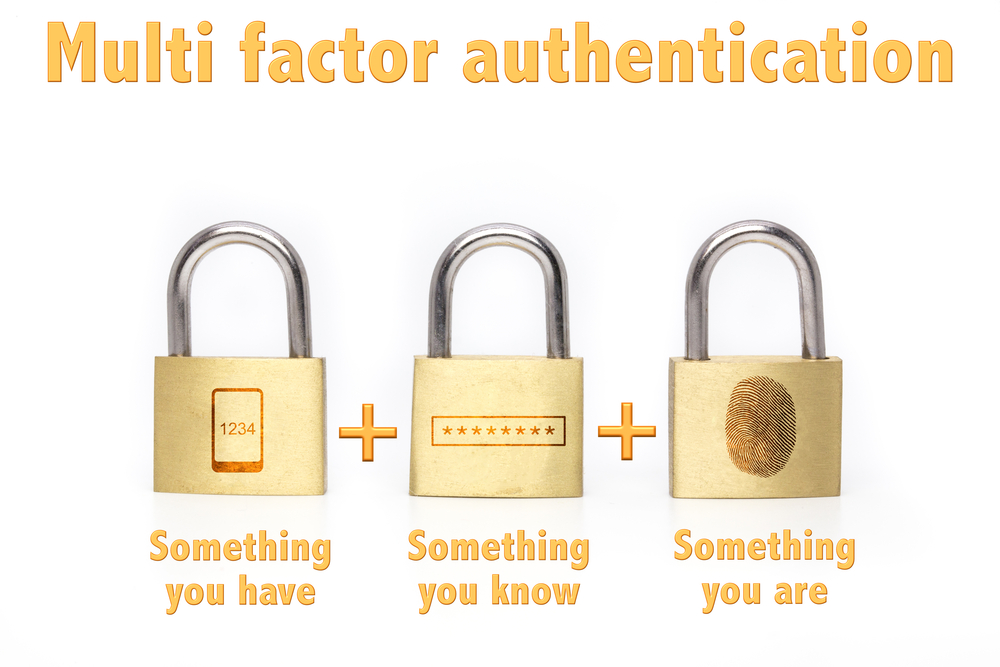
That being said, there seems to be a growing demand for even more secure solutions. Two-factor authentication combines security with convenience, although it is not a perfect concept by any means. Security experts feel multi-factor authentication, also referred to as three-factor authentication, needs to become the new industry standard moving forward. Adding multiple layers of authentication will result in stronger security and fewer chances of letting consumer data fall into the wrong hands.
Some people may be wondering how we can achieve three-factor authentication in a convenient manner. It is important to understand every additional layer of authentication has to be unique. Passwords, PIN codes, and even two-factor authentication codes can be mimicked by criminals. Keeping that in mind, there are very few options on the table to create a unique third layer unless it pertains to the end user himself.
Fingerprint authentication is becoming somewhat popular in the mobile industry. Unlocking one’s device can be done through a pin code, gesture, or a fingerprint scan, which adds another layer of security. Fingerprints are unique to every individual on this planet, making them a possible candidate to ensure three-factor authentication becomes the new norm. Some experts oppose using fingerprints, though, as they can be lifted from random objects at an individual’s house.
Additional solutions range from using a user’s hand configuration to a palm vein scan and even using retinal scans. All of these biometric measures are unique to the end user, and much harder to mimic. On the other hand, these measures may not be seen as “convenient” by the mainstream. On the other hand, security should always trump convenience, as security should be the top priority for both users and service providers alike. Our society has grown accustomed to unprecedented levels of convenience, which allows for data breaches to happen on a regular basis.
Smart people may have enticed every layer of three-factor authentication is a different security measure compared to the previous one. Passwords and Pin codes are the basic requirement. Using a unique authentication token adds an extra layer of security. Biometric identification ensures the first two measures can only be entered by the actual user, rather than someone impersonating another individual. It is not unlikely a fourth and fifth layer will be added in the future, though. Adding more security to our digital lifestyle is an absolute must, that much is certain.
If you liked this article, follow us on Twitter @themerklenews and make sure to subscribe to our newsletter to receive the latest bitcoin, cryptocurrency, and technology news.