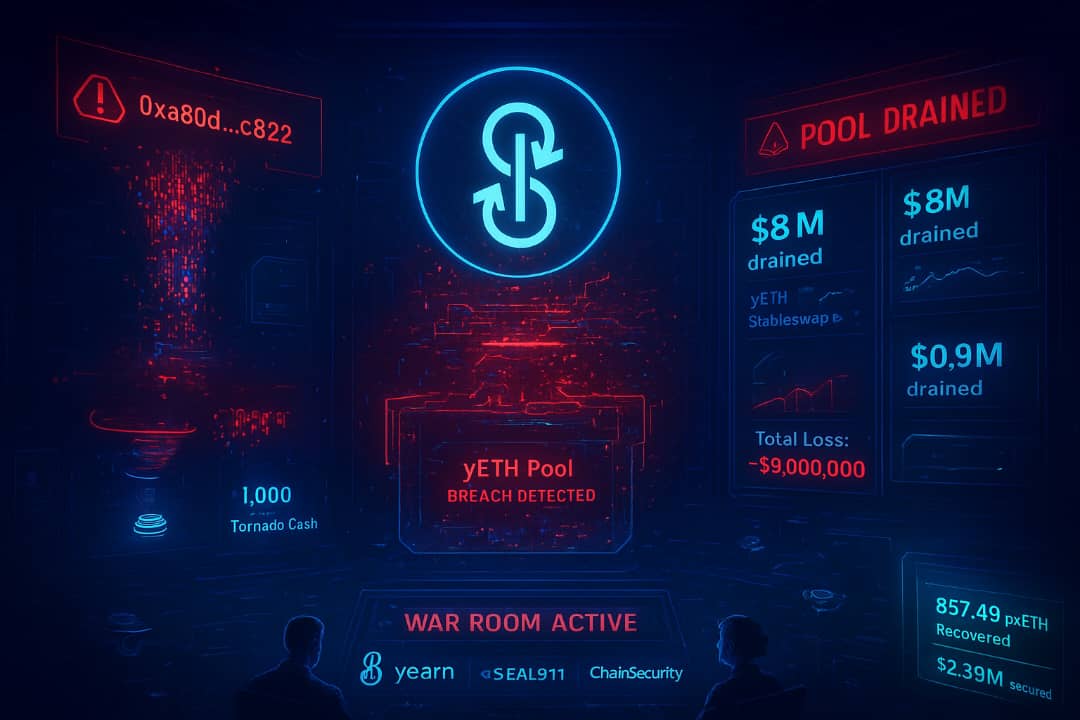
Yearn Finance is facing one of its largest incidents in recent years after a sophisticated exploit drained roughly $9 million from its ecosystem.
The attack, which struck late on November 30, targeted a custom-built yETH stableswap pool and allowed an attacker to mint an almost unlimited supply of yETH tokens in one move. The breach triggered an emergency response from Yearn’s internal team and external security partners, marking one of the most complex investigations since the recent Balancer exploit.
A Single Transaction Turns Into a Major Breach
According to on-chain alerts, the attacker exploited the yETH pool at 21:11 UTC, triggering a flaw in the pool’s custom contract. The bug enabled the minting of a massive amount of yETH, which was then rapidly swapped to drain liquidity.
PeckShield first flagged the attack, confirming that the exploit allowed the minting of a near-infinite number of yETH tokens. The attacker leveraged these newly created tokens to empty the pool almost instantly, all within a single transaction.
Early estimates now show:
- $8 million was drained from the main yETH stableswap pool
- $0.9 million was lost from the yETH–WETH pool on Curve
- Total loss: ~$9 million
Yearn later confirmed the details through its official communication channels.
Funds Route Through Tornado Cash as Attacker Moves Quickly
Shortly after the exploit, the attacker began moving funds across the network. Approximately 1,000 ETH (~$3 million) was routed through Tornado Cash, a common laundering destination for on-chain attackers.
The exploiter’s address, 0xa80d…c822, still holds crypto assets valued at about $6 million, according to chain trackers.
The swift movement of funds indicates a well-prepared and experienced actor, a pattern consistent with the Balancer-style complexity that analysts have already noted.
Yearn Confirms Incident Isolated to a Custom Contract
Yearn Finance released multiple statements within hours of the attack, confirming that:
- The contract affected is a custom implementation of stableswap code
- It is not used in any other Yearn product
- Yearn V2 and V3 vaults remain safe
At 21:11 UTC on Nov 30, an incident occurred involving the yETH stableswap pool that resulted in the minting of a large amount of yETH. The contract impacted is a custom version of popular stableswap code, unrelated to other Yearn products. Yearn V2/V3 vaults are not at risk.
— yearn (@yearnfi) December 1, 2025
The team emphasized that the exploit is isolated to this single yETH pool and does not impact the broader Yearn ecosystem, a critical clarification aimed at calming users amid the sudden shock.
Yearn noted that the codebase exploited in this attack is completely separate from all other vaults, products, and strategies currently active on the platform.
Investigation Begins: SEAL911 and ChainSecurity Join the War Room
A full-scale response effort is now underway. Yearn activated a war room alongside:
- SEAL911, a rapid-response crypto security organization
- ChainSecurity, Yearn’s audit partner
The teams are now running an active, ongoing investigation. Yearn urged affected users to open a support ticket on Discord for direct assistance.
yETH update: With the assistance of the Plume and Dinero teams, a coordinated recovery of 857.49 pxETH ($2.39m) was performed. Recovery efforts remain active and ongoing. Any assets successfully recovered will be returned to affected depositors.https://t.co/xaClNhd0C0
— yearn (@yearnfi) December 1, 2025
Given the complexity of the exploit, Yearn warned that the postmortem may take time. Internal analysts have already stated that the attack appears to match the “high-complexity pattern” seen in November’s Balancer exploit, which also relied on intricate token mechanics and custom contract behavior.
Yearn asked the community to bear with the team as the full analysis is prepared.
Early Findings: How the Exploit Worked
Though the full postmortem remains in progress, preliminary analysis suggests the attacker manipulated the yETH pool’s minting logic. The custom code allowed the perpetrator to trigger a flawed conversion path that produced an outsized amount of yETH tokens.
In simpler terms:
The attacker found a way to trick the contract into thinking more collateral existed than was actually present.
This created:
- A massive supply of synthetic yETH
- Instant liquidity access
- A fast exit route via Curve pools and Tornado Cash
Security experts point out that such attacks usually require:
- Deep protocol knowledge
- Precision execution
- Understanding of stableswap model edge cases
Yearn’s internal team and its external partners are now replaying the exploit step-by-step to confirm the exact mechanics.
Recovery Efforts: $2.39M Already Retrieved
While the loss is significant, Yearn shared a major update: a recovery of 857.49 pxETH, valued at $2.39 million, has been successfully executed.
This coordinated effort involved the Plume and Dinero teams, who assisted in tracing, securing, and returning the assets.
Recovery operations remain active, and Yearn has pledged that any funds retrieved will be returned directly to impacted depositors.
The team also noted that additional recovery attempts are in motion, with the goal of maximizing restitution for affected users.
Community Response: Shock, Concern, and Praise for Transparency
The crypto community reacted quickly, with analysts, developers, and users noting both the severity of the exploit and the transparency of Yearn’s communication.
Yearn’s rapid updates and clear threads addressing the incident were highlighted as strong crisis management. Security researchers also praised the immediate involvement of SEAL911 and ChainSecurity.
Still, the incident reignites broader concerns about:
- The risks of custom smart contract code
- The strain on DeFi protocols as attackers grow more sophisticated
- Increasing similarity to multi-vector attacks seen throughout 2024 and 2025
For Yearn, the incident raises questions about future audits and how emerging contract models should be handled.
The investigation continues. Yearn Finance is expected to release:
- A full postmortem report
- A breakdown of the attack vectors
- Mitigation plans and upcoming security upgrades
The team also plans to share detailed recovery updates as more assets are tracked and secured.
For now, Yearn’s message remains consistent:
The exploit is isolated, user vaults are safe, and recovery efforts are ongoing.
Disclosure: This is not trading or investment advice. Always do your research before buying any cryptocurrency or investing in any services.
Follow us on Twitter @themerklehash to stay updated with the latest Crypto, NFT, AI, Cybersecurity, and Metaverse news!